Ransomhub Targets Spanish Slaughterhouse Biogas SCADA System
Ransomhub, a nascent ransomware-as-a-service (RaaS) operation, has allegedly compromised the supervisory control and data acquisition (SCADA) system of a Spanish slaughterhouses bioenergy plant that processes slaughterhouse waste, underscoring the growing threat of cybercrime targeting industrial control systems (ICS) in critical infrastructure sectors.
Ransomhub's Attack on Matadero de Gijón's SCADA System
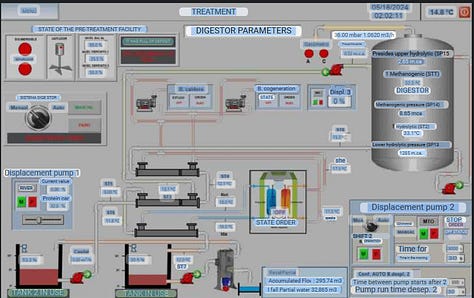


Ransomhub claimed unauthorized access to the SCADA system controlling the digester and heating processes at Matadero de Gijón's bioenergy plant, which converts slaughterhouse waste into biogas. The group provided screenshots showing their ability to manipulate these critical industrial controls. While the exact scope of the breach is unclear, with estimates ranging from 15 GB to 400 GB of data, the compromised SCADA system poses significant operational risks. Ransomhub, which emerged in February 2024 as a RaaS operation, utilizes Golang and C++ for its locker component and employs a combination of asymmetric (x25519) and symmetric (AES256, ChaCha20, XChaCha20) cryptographic algorithms to efficiently encrypt victim data. The group's targeting of ICS environments using stolen VNC credentials purchased from Initial Access Brokers on Russian forums highlights the growing interest of ransomware actors in exploiting the vulnerabilities of connected OT systems.1
RansomHub TTPs
Here is a detailed analysis of the Ransomhub ransomware group and their tactics, techniques and procedures (TTPs):
Ransomhub is a relatively new ransomware-as-a-service (RaaS) operation that emerged in February 2024. They were first announced on the RAMP cybercriminal forum by a user named "koley".
Ransomhub's ransomware is written in Golang and C++. It supports encryption on Windows, Linux, ESXi and MIPS architectures. The ransomware uses a combination of asymmetric (x25519) and symmetric (AES256, ChaCha20, XChaCha20) cryptographic algorithms.
The Ransomhub encryptor has some similarities to the ALPHV/BlackCat ransomware in its configuration, such as requiring a strong passphrase to decrypt an embedded config. However, there are also significant differences, with Ransomhub employing additional obfuscation measures not seen in ALPHV.
Ransomhub follows a RaaS model where the core group develops the ransomware and leases it to affiliates. A unique aspect is that Ransomhub pays the affiliates first (90% of ransom payments), who then pay Ransomhub (10%) - a different model from most other RaaS operations.
The group has strict rules for affiliates, including prohibiting attacks on non-profits and entities in CIS states. Affiliates who violate the rules are banned. This resembles the approach of some other prominent Russian-speaking ransomware groups.
Since claiming their first victim in February, Ransomhub has been scaling up their operations rapidly. As of April 2024, they had compromised 45 victims across multiple countries, with the US being most heavily targeted. At this growth rate, Ransomhub is poised to become one of the most prolific ransomware groups.
There are theories that Ransomhub may be linked to the ALPHV/BlackCat group, potentially as a rebrand after ALPHV's disappearance. This is based on similarities in their rules, targets, and the timing of ALPHV closing down their operation. However, technical analysis shows significant differences in the ransomware code, so a direct connection remains unconfirmed.
Ransomhub has been connected to the high-profile attack on Change Healthcare, which was initially compromised by an ALPHV affiliate. After ALPHV allegedly conducted an "exit scam" without paying the affiliate, the affiliate (known as "Notchy") appears to have taken the stolen data to Ransomhub to extort the victim a second time.
In summary, while Ransomhub is a newer entrant to the ransomware ecosystem, they have quickly established themselves as a major threat with a technically sophisticated offering and a growing affiliate network. Their unique payment model and targeting of high-value sectors like healthcare make them a group to watch closely. While some of their TTPs resemble other RaaS groups, particularly from the Russian-speaking cybercriminal community, they also show distinct characteristics. Ransomhub's meteoric rise underscores the continued evolution and diversification of the ransomware landscape.2 3 4 5
Ransomhub Attacking Industrial Control Systems To Encrypt Data (cybersecuritynews.com)
Dark Web Profile: RansomHub - SOCRadar® Cyber Intelligence Inc.
Forescout details RansomHub group emerges as latest cyber threat post-Change Healthcare attack - Industrial Cyber
Change Healthcare and RansomHub redefine double extortion (barracuda.com)
RansomHub Responsible for Christie's Hack, Threatens Data Leak (secureworld.io)


